Google Cloud liên tục đổi mới và đầu tư đáng kể vào khả năng ngăn…
Improve email security in Gmail with default TLS protocol and other new features
What’s changing
Recently, Google Security blog protocol usage statistics Transport Layer Security (TLS) grew to more than 96% of total traffic seen by the Chrome browser on Chrome OS. The blog post also highlights an important goal: enable TLS by default for Google products and services to ensure that TLS works properly.
Gmail already supports the TLS protocol, so it's more secure if a simple Mail Transfer Protocol (SMTP) mail connection can be secured via TLS. However, to encourage more organizations to increase their email security, and to further our goal of enabling TLS by default, Google has made the following changes:
- TLS connection for email will be enabled by default
- Admins can now test their SMTP outbound mail routing configuration in the Admin console prior to deployment. They no longer need to wait for notification messages.
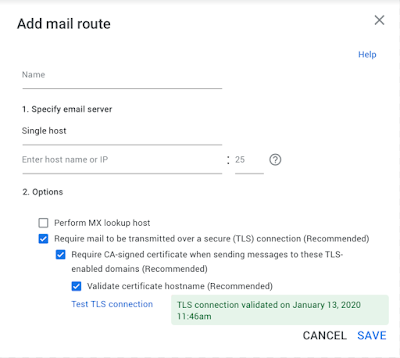
While administrators can always require TLS encryption for mail routes at any time, it was previously disabled by default. Note that existing mail routes will not be affected by these changes.
Who’s impacted
Admins
Why it’s important
Google always recommends that administrators enable existing mail security features, including SPF, DKIM, and DMARC, to help protect end users. Google also recommends that administrators enable MTA Strict Transport Security (MTA-STS), which improves Gmail security by requiring encryption and authentication checks for email sent to their domain. Enabling TLS by default on new SMTP mail routes strengthens the client's security layer and allows administrators to test connections before enforcing TLS on existing routes making it easy for them to deploy new SMTP mail routes. security policy best practices.
This change will not affect previously created mail routes.
More details
TLS is enabled by default on all new mail routes
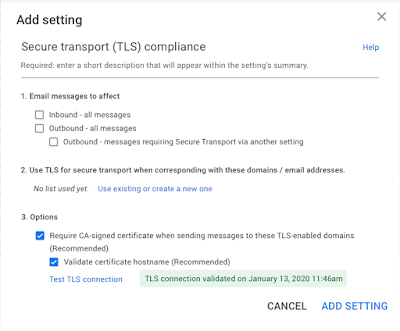
With TLS enabled by default for new mail routes, all certificate validation requirements are also enabled by default. This ensures that the recipient server has a certificate issued to the correct server that has been signed by a trusted Certificate Authority (CA). See more details on how we changed the requirements for trusted CAs below.
Admins can still customize their TLS security settings on newly created mail routes. For example, if mail is forwarded to a third-party mail server or to a mail server that is hosting an internal CA certificate, the administrator may need to disable CA certificate validation. It is not recommended to disable CA certificate validation or even disable TLS altogether. We encourage admins to check their TLS SMTP configuration in the Admin Console to authenticate TLS connections to their mail servers before disabling any suggested validations. See more details on how to test TLS connections in the Admin console.
Certification bodies don't trust Gmail
In the past, the Google Security Blog has highlighted cases where Chrome no longer trusts root CA certificates used to intercept traffic on the public internet, and Chrome doesn't trust specific CAs.
If these scenarios happen in the future, these certificates will also be distrusted by Gmail. When this happens, messages sent using TLS-encrypted routes that enforce certificates signed by the CA may bounce if the CA is no longer trusted. While the list of root certificates trusted by Gmail can be retrieved from the Google Trust Services repository, we encourage admins to use the Check TLS Connection feature in the admin console to confirm whether the certificate has been distrusted.
Check TLS connection in Admin console
Admins can now use the new TLS Connection Test feature to verify if a mail route can successfully establish a TLS connection with full authentication to any destination such as a mail server on-premise or third-party mail forwarding, before enforcing TLS for it.
Getting started
Admins
Set up TLS
TLS will be ON by default for all new mail routes. We recommend that administrators review all their existing routes and also enable all recommended TLS security options for these routes.
Check TLS Connection
Admins who want to request a secure TLS connection for email can now verify that the connection to the recipient's mail server is valid simply by clicking the Test TLS Connection button in the Dashboard for administrators; they no longer need to wait for emails to bounce.
See more about Requires mail to be routed through a secure connection (TLS) and add routing in the Help Center.
End users
- There is no setup for the end user.
Deployment speed
- Rapid and Scheduled Release: Extended rollout (potentially longer than 15 days for feature exposure) starting April 2, 2020
Available now
- All G Suite customers (Google Workspace)
Source: Gimasys