Tại Google Cloud, Google cam kết cung cấp cho khách hàng sự lựa chọn hàng…
Cloud Identity: Centralized User, Device, and Application Management
In the article about Google Cloud Identity Last time, we gave a general introduction to Google's identity recognition and device management services – including the concept and available features. Overall, Cloud Identity provides businesses with a service that helps control login, access documents, applications. Thanks to this feature, it helps business managers can consolidation and consolidation of control user access at a single platform. This article will help you dig deeper into the reasons and benefits of including Cloud Identity in your business applications.
1/ Why have Cloud Identity?
With today's strong development and application of information technology, businesses have been rapidly moving to the cloud computing environment, or at least a hybrid environment (combining the use of basic infrastructure). traditional and cloud infrastructure). According to reports on mobile device usage (Mobile Analytics Report) by Citrix, the average user uses at least three devices and always needs quick access to work-related apps so they can do it wherever, whenever they need it. That means the challenges that enterprise IT teams face when technology is always in a state of rapid change.
Therefore, the need to control who has access to applications and data warehouses of enterprises is becoming increasingly urgent and complex. Checking inventory data with colleagues on the other side of the globe, supporting customers right at their office instead of moving to the place, checking email right on the plane… can say the applications are used. Building on the Cloud not only changes the way we work, but also changes the way businesses perceive security.
The problem is not one's own. Even the "giant" in the technology industry - Google - must face these challenges first. And from my experience, Google has launched Cloud Identity – not only helping staff have been Simple access, security but also gives the manager business one solution centralized user control.
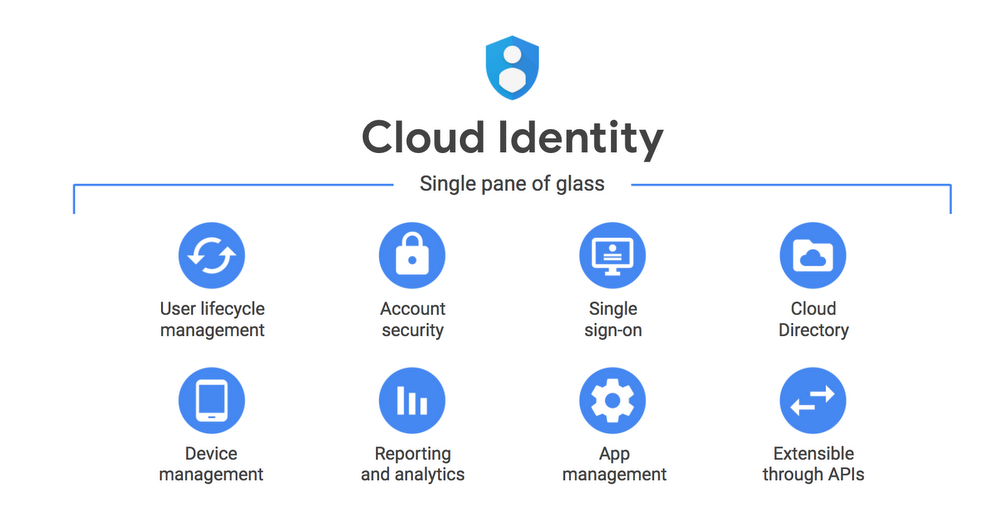
2/ Benefits of applying Cloud Identity in enterprises
2.1. Simple for users, effective for managers
Cloud Identity gives your users - employees a simple access tool, with just one click, they can access the resources they need. As a result, employees can work anytime, anywhere, on any device. This helps them focus on their work, while admins can manage the identities of visitors, associated applications or devices in use – all in one place. , whether they have just joined, moved or left the company.
Cloud Identity's Single Sign On (SSO) feature also supports SAML 2.0, OpenID, G Suite applications such as Docs, Drive, etc. and also supports external applications such as Salesforce, SAP SuccesFactors, Box,…
For businesses that are using the resources of Google Cloud PlatformCloud Identity also gives admins control over both users and groups in hybrid environments.
2.2. Work from anywhere but data safety is always guaranteed
It's not just about building information systems, connecting end users to the resources they need, whatever those resources are, where they are located - is also an essential role of the IT department. Now, the image of an employee having to be at the office every day, working with an old desktop computer has gradually been replaced by the image of them sitting at a coffee shop, co-working space, or even Even at the airport, with my phone and laptop. It is this new way of working that will be a suggestion for businesses to design their login and security management processes.
Cloud Identity brings effective and tight mobile device management, for both Android & iOS devices with a lot of features such as account wiping (deleting all data in the account if found to be dangerous. security threat) or automatically set up passwords for users. Business admins can use a centralized, integrated admin page to do a variety of things: Lock screen, find device, enforce (mandatory) two-step verification, and lock security just in case fraudulently steal information, or manage the use of the Chrome browser.
Admins can also view security analysis and reports for other factors such as: abnormal logins, logins to third-party applications, websites or extensions; audit (audit) user activity.
2.3. Cloud Identity is an open ecosystem with open standards
Enterprises choose solutions from suppliers Directory Service* Traditionally, there is often no choice but to use only that provider's platform and protocol (this is also known as "vendor lock-in"). But this is not, and should not be, the standard that businesses choose their management solutions for. Instead, opt for an open platform from which you can leverage any solution that benefits your business. A good cloud-based identity management platform should give IT the independence they need, while ensuring centralized access management.
*Directory (or Directory service) is a directory service, applied in storing information and data according to the Directory organization architecture and centrally managing objects (shared applications, users, printers, ...), thereby helping to Simplify resource identification and management.
Likewise, Google Cloud Identity is built to be an open ecosystem as Google has committed to open standards in the security space tell honey. Businesses can easily integrate Cloud Identity with other traditional or cloud-based directory solutions. Currently, Google is also working with a network of many identity service providers to help businesses choose the solution that best suits them, meeting deployment requirements in a hybrid environment.
2.4. Meet all your business requirements with just one solution
Cloud Identity is built to give businesses the tools they need to protect users, devices, and data from a single place, thereby not only improving work efficiency, but also reducing risk. data theft.
HealthChannels is a unit that has put Cloud Identity into the application and met its management requirements. Daniel Tehrani – Vice President of Information Technology at HealthChannel shared: “At HealthChannel, we help more than 15,000 healthcare workers in hospitals and clinics. This means helping train, assign tasks, and move hundreds of employees each month. Meanwhile, the team still has to ensure transparency and control over which applications they are allowed to access. Although the team is only 6 people, Cloud Identity has helped us manage employee work cycles effectively.”
Conclusion
Despite bringing a lot of practical benefits, in general, the application of Cloud Identity in Vietnamese businesses is still not popular. A big part of the reason is that we are still not fully aware of the importance and benefits of managing users and resources in the enterprise. In the current era of technology development, it is always accompanied by potential security risks, so it is never too late to centrally manage resources and apply the benefits of cloud computing. You can Register for free use any time, or at least learn more about them.
Source: Gimasys



