Google Cloud liên tục đổi mới và đầu tư đáng kể vào khả năng ngăn…
Data protection: Secure data when storing and using

In first episode of the Cloud Security Podcast, a pleasure to speak with Nelly Porter, Group Product Manager of the Cloud Security group.
In this interview, Anton, Tim and Nelly consider an important question about data security: How can we handle extremely sensitive data in the cloud while keeping it protected against insider access? Turns out it's easy for Google Cloud.
Some public cloud customers worry about their data in a variety of ways. And they have all kinds of sensitive data, from healthcare records, to credit card numbers, company secrets, etc. For some organizations, entrusting that data to a Public cloud provisioning is considered risky. Or, some organizations may have data that is extremely sensitive or highly damaging, if lost or stolen.
In the past, most companies would collect the data, process it themselves, and do any conversion or aggregation on-site. They know who is using the data, how and when. That makes roles and responsibilities really clear.
With the cloud, everything has changed. The ability to store and use is much better, but it also leaves some companies unable to manage data. Cloud security is a shared responsibility model: some is handled by the customer, some is handled by the provider.
For example, let's say you've collected a bunch of customer behavioral data, purchasing patterns, and purchase history. You've uploaded it all to Cloud Storage – it's encrypted and you can keep the keys (e.g. via Google Cloud EKM); you are safe. This will work for many types of sensitive and regulated data. Correct?
Next, you start performing data analysis, perhaps even training an AI model on your data. Now that you're using the data, it's no longer protected by the same encryption. You still get the advantage of reserved memory, but the data is not obfuscated, as may be desired by some clients in some use cases.
Google Cloud Platform Solve this difficult problem by confidential computing, allowing you to complete the cycle and keep data protected in transit, storage, and use. Although it started with CPUs, they also expanded the service to include GPUs and Accelerators, so your data is protected wherever you are.
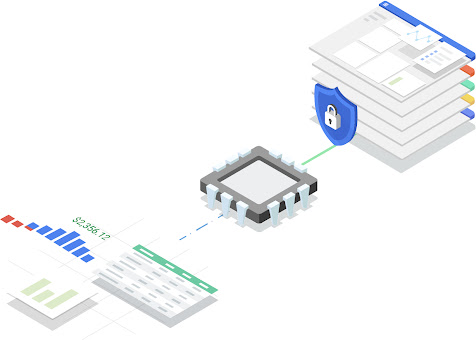
Confidential computing becomes possible with suitable CPU hardware, allowing data encryption during load and use. And because this is a hardware upgrade, nothing needs to be changed with your code to take advantage of it.
The alternative for most companies would be to just process and process ultra-sensitive data on-premise, which means missing out on the scale, functionality, and reliability of public cloud infrastructure. With this improved cryptographic isolation, companies of all types can use sensitive data across services and tools. The only downside is a slight increase in latency and increased cost.
Whether you're handling highly regulated financial services data, sensitive photos from your customers, or need to protect highly valuable intellectual property, Let's check the secret calculation and hear more about how it works on this episode of the Cloud Security Podcast.
Source: Gimasys