Đại dịch vừa qua đã khiến lưu lượng truy cập tổng đài chăm sóc khách…
Google shares how to help businesses modernize security on the Cloud
During the first few months of the COVID-19 pandemic, many organizations' digital transformation efforts are expected to slow down. Instead, Google sees many businesses accelerate their adoption of Cloud-based services to help them manage and address emerging priorities in the new normal, including workforce allocation and New digital strategy.
Advanced security tools to ensure rule compliance and data security
An increasing number of companies, especially those in highly regulated industries, want to adopt the latest cloud technologies, but they often encounter roadblocks due to regulatory compliance requirements or permissions. Strict data privacy. Last month, Google introduced two new capabilities that help businesses securely leverage all that the cloud has to offer while simplifying security operations.
Guaranteed Government Workloads, currently in private beta, allows those in regulated industries such as publicly configuring regions and deploying sensitive workloads to regulatory requirements. their security and compliance — in just a few clicks. Unlike the traditional “government cloud,” Guaranteed Workloads remove the trade-off between meeting compliance requirements and having the latest capabilities in your cloud.
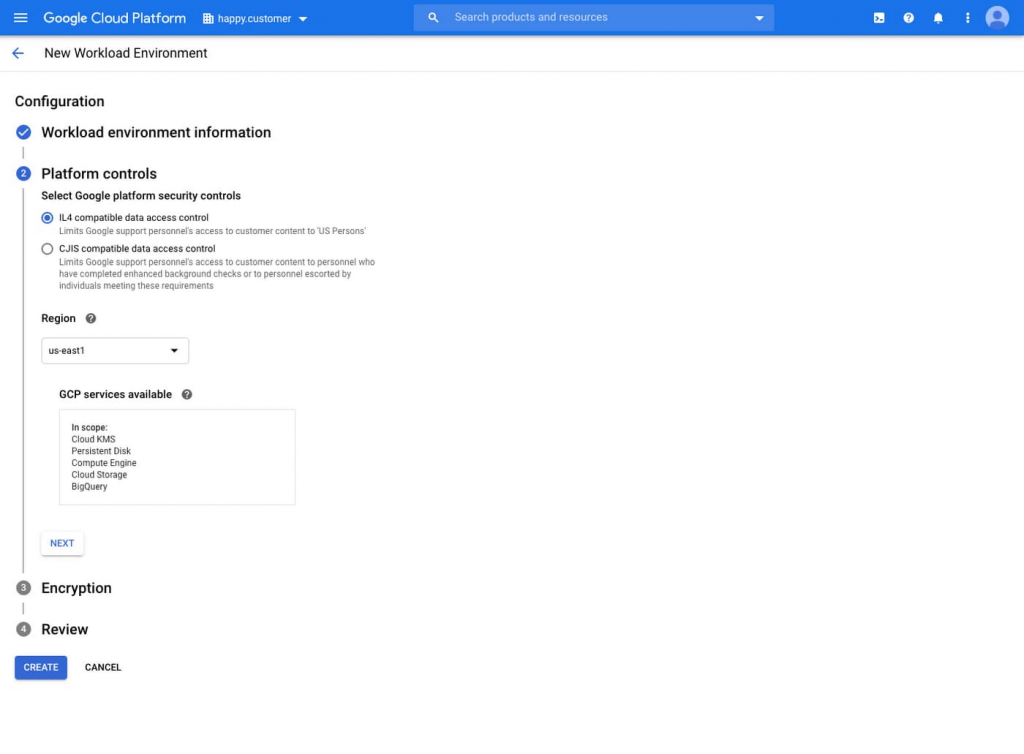
Confidential VMs, the first in Google's Confidential Computing portfolio, help you protect your sensitive data in the cloud. Encrypted data is at rest and in transit, but traditionally, customer data has to be decrypted for processing.
Confidential Computing is a breakthrough technology that encrypts data in use — while it is being processed. Confidential VMs take this technology to the next level by providing in-memory encryption so you can keep your workloads isolated in the cloud. With the beta launch of Confidential VMs, Google is the first major cloud provider to offer this level of security and isolation, while giving you a simple, easy-to-use option for your applications. newly built and your "lift and move".

Cloud-based, CA management for Devops and IoT world
Recently, many enterprises are interested in using Public Key Infrastructure (PKI) in DevOps and IoT device management. But one fundamental problem with PKI remains: it's hard to set up Certificate Authorities (CAs), it's even harder to do it reliably at scale. These issues are at the heart of these growing use cases.
To help, Google announces beta availability Certificate Authority Service (CAS) of Google Cloud—a highly scalable and out-of-the-box service that simplifies and automates the management and deployment of private CAs and meets the needs of modern developers and applications. With CAS, you can offload the time-consuming cloud tasks associated with running a private CA, such as hardware provisioning, infrastructure security, software deployment, availability configuration Advanced, disaster recovery, backups, etc., allow you to set up a private CA in minutes, instead of months that can normally take to deploy.
A single pane of glass into your security situation
Protecting your users, data, and applications while remaining compliant can be a challenge. Add to that the need for remote workforce management and increased complexity. With Cloud Security Command Center (SCC), Google's own management platform, you can prevent and detect abuse of your cloud resources, centralizing security findings from Google's services. Google Cloud and partner products, and detect common misconfigurations, all in one easy-to-use platform.
Recently, Google announced the Premium tier for Security Command Center to provide even more tools to protect your cloud resources. It adds new capabilities that allow you to:
- Detect threats using Google intelligence for (GCP) logs and containers
- Large collection surface of misconfigurations
- Perform compliance scans and reports automatically
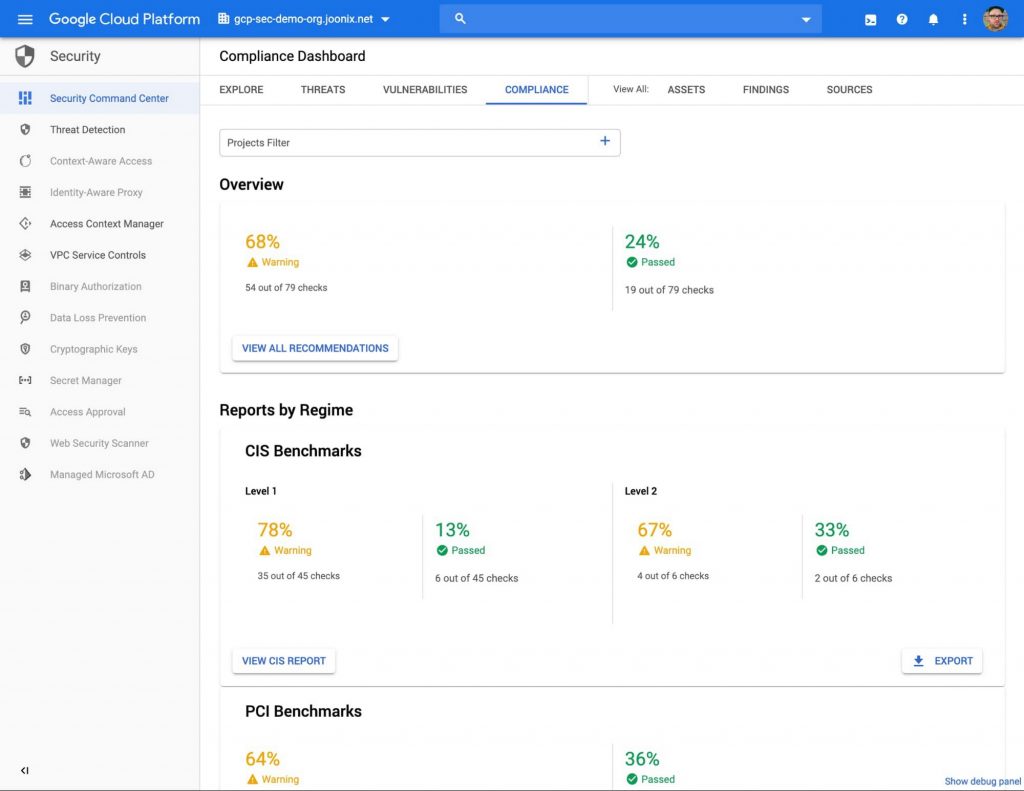
These features help you understand your risk on Google Cloud, verify that you've configured your resources properly and securely, and document it for anyone who requests it.
Collaborate with endpoint and orchestration partners
As part of its mission to enhance operational simplicity and security, Google is committed to working with its security partners to help you on this journey. This week, Google will be announcing new integrations and marketing activities with Palo Alto Networks on their xSOAR Marketplace.
Additionally, Google announced an expanded partnership with Tanium, which is integrating and delivering Chronicle with their endpoint security and management solution. This integrated solution, sold by Tanium, links endpoint data from Tanium with other telemetry, such as DNS and proxy data in Chronicle, to provide a broader, clearer picture of relationships threats in business. By default, Chronicle retains Tanium telemetry for one year, improving your ability to investigate incidents in the long run.
Simplify protection against DDoS and web attacks
Google is simplifying how you can use Google Cloud Armor to help protect your websites and apps from exploit attempts, as well as distributed denial of service (DDoS) attacks. With Cloud Armor Managed Protection Plus (in Beta) you get access to DDoS and WAF services, managed rule sets, and other services at predictable monthly rates.
Automate safer deployments with blueprints
While these new products offer real benefits, you also need to configure your cloud deployment to meet your own unique security and compliance requirements. Google will publish a comprehensive design of the new Google Cloud security platform, providing selected guidance, effort, and accompanying automation to help build a secure starting point for Google Cloud deployment. It will launch as the foundation of the Google Cloud security best practices resource center, a new web destination that delivers world-class security expertise from Google and its partners in the form of security blueprints, manuals, books, etc.
A better, safer normal go together
Protecting your business requires constant growth, and events so far in 2020 have made that even more apparent. With compliance automation, simpler security operations, and better protection for employees and customers, Google is committed to helping businesses adjust and evolve to make today's new normal the normal. usually safer.
Source: Gimasys