Số hóa bùng nổ mạnh mẽ kéo theo khách hàng ngày càng yêu cầu cao…
How Google Cloud Platform helps you control threats
Why does Google keep talking about Security all this time? Hasn't anyone been able to fix these vulnerabilities?
You've heard these questions somewhere, whether from your boss, or a member of the board of directors, or just from friends. You then attempt to explain why security in the cloud is so complex and challenging, the ongoing arms race. But you're right: It's complicated, and difficult.
As a security administrator today, you can spend a lot of time focusing on gathering information: what's happening, new vulnerabilities emerge, what threats are present in your environment. and how to fix them. And you probably already have several dozen tools available to measure, analyze, collect, and search through your data.
Right now, with your existing toolset, you believe you have good control over your on-premise systems and defenses. But above all, you can get tangled up in inconsistent data patterns, stale data, and messy information coming from different tools. So consolidating and normalizing the data sources, really gives you a full picture.
Then you add cloud systems and it gets even more complicated. To summarize National Cybersecurity Awareness Month, Google details some of the most recently developed security features, Event Threat Detection, available right in the session. beta and highlights some information that can help you reduce the complexity of your organization's security and improve your security layers.
Visibility and control, and stopping threats
With the new Cloud Security Command Center (Cloud SCC), Google offers a flexible platform to give you broad visibility and quick response. In addition to potential threat and risk management, Cloud SCC focuses on proactive defense, showing you detected threats and the path to more comprehensive security for your cloud resources. your. It integrates with existing security solutions you already use and Google Cloud security tools. Also its API is accessible to you and your provider, so any additional data is easy to integrate.
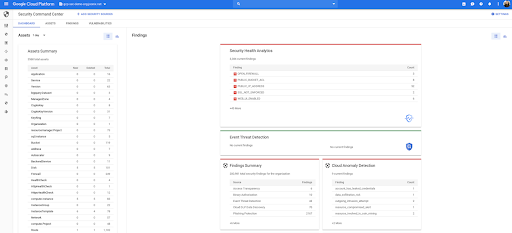
The model above is a centralized dashboard to prevent, detect, and respond to threats, with the current state of the system that you can change based on your needs. For example, you can centralize resources to get a holistic view of every firewall, network, disk, bucket, etc. in your organization.
You can also shape your opinion based on findings (outcomes) of vulnerabilities in the environment Google Cloud Platform your (GCP). Recently, we went out Dashboard Vulnerabilities to display results from Security Health Analytics. It is an integrated security product that helps you identify misconfigurations and compliance violations in your GCP resources, and recommend action.
Reduce your risk of facing threats with Event Threat Detection
Reducing your risk of facing threats goes hand in hand with being able to react quickly to attacks in your environment. Today, Google announced the beta of Event Threat Detection, a security product that integrates into Cloud SCC and is inspired by how Google protects itself. We want to scale and intelligence to help you protect your systems and improve your security.
Event Threat Detection helps you detect threats in system logs and send high-risk threats to SIEM (Security Information and Event Management system) for further investigation. It can also save you time and money by focusing your attention on the most worrisome cloud-based threats.
Thanks to the rise of cloud computing, Google has seen an increase in the number of customers using VPC Flow, Cloud DNS logs, Cloud Audit logs, and system logs distributed on GCP. Event Threat Detection uses Google's intelligence to confront threats surfaced in these logs, including anomalous IAMs, malware, crypto, DDoS, and powerful SSH.
When Event Threat Detection finds a threat in your logs, it shows up as a detection on the Cloud SCC dashboard. If you need further analysis of any of these threats, you can submit them to your SIEM, saving you time and money as Event Threat Detection finds you potential dangers you need to investigate further.
Event Threat Detection integrates with Cloud Functions to make it easier for you to retrieve results for the SIEM of your choice. You can also use Cloud Functions to automate responses and changes to Event Threat Detection findings. Watch more videos below:
Responding to threats
Once threats have been detected, the obvious final step is taking action against them. To help speed up response, you can set up automatic actions each time a threat is detected. When Cloud SCC detects an anomaly or an active threat, you can ask it to change the VM configuration, possibly cutting the VM off from other parts of your network. You can also change the firewall rules automatically. Using these events to trigger Cloud Functions, you can set up any response you want, fully automated. Also, you can send metrics and crash data to your own Stackdriver or SIEM to ensure the incident response team has all the information they need.
Combined, these features give you the power to structure and organize the data you collect, which is key to securing large organizations' cloud operations. Cloud SCC allows you to create tags for items to assist with project-based request or incident response and to aid in creating custom dashboards. Critical goal: to give you the information you need quickly, so you can take the most timely actions.
Details about Cloud SCC
Now that you have an overview of how Cloud SCC and Event Threat Detection can help you keep your organization safer, here are some more documents highlighting built-in Google security features: integrated into the Cloud Security Command Center, how they work, and how they can help you improve your security posture:
- Find and fix misconfigurations on Google Cloud resources with Security Health Analytics
- Prevent data leaks with Cloud Data Loss Prevention
- Detect and act on unusual security events with Cloud Anomaly Detection
- Scan and detect web application vulnerabilities with Cloud Web Security Scanner
These blogs have step-by-step instructions with screenshots, and each has a companion video. Take a look and let us know if there are any other problems and solutions that you would like to elaborate on.
To get started with Cloud Security Command Center, watch the video below:
If you're new to GCP and want to try these products, just start a free trial of GCP, enable Cloud SCC, and enable built-in security products, like Event Threat Detection. You can read the reasons If you are an existing Cloud SCC customer, simply enable Event Threat Detection and our other security products from Cloud SCC. For more information about Event Threat Detection, Read our brochure.
Source: Gimasys