Google Cloud liên tục đổi mới và đầu tư đáng kể vào khả năng ngăn…
Featured Application: Basic Device Manager brings basic tracking to all computers
What’s changing
Với lần ra mắt này, tất cả các thiết bị máy tính để bàn đăng nhập vào G Suite (Google Workspace) sẽ được quản lý thiết bị cơ bản theo mặc định. Điều này có nghĩa là khi người dùng đăng nhập vào G Suite thông qua bất kỳ trình duyệt nào trên thiết bị Windows, Mac, Chrome hoặc Linux, thiết bị sẽ được đăng ký với quản lý điểm cuối của Google. Điều này sẽ tự động xảy ra khi đăng nhập -không yêu cầu bất kỳ hành động hoặc phần mềm người dùng nào khác được cài đặt trên thiết bị.
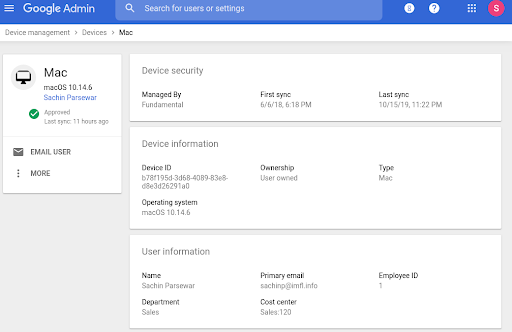
Once a device is registered with basic device management, the admin can see the device type, operating system, first sync time and last sync time in the Admin console pellets. They can also log out the user from that device.
This provides the basic benefits of device management without the added cost or requirement of installing agents or profiles. We are also improving the filters available in the device list that can help with endpoint verification and Context-Aware Access implementation. See more information below.
Who’s impacted
Admins
Why use
Basic device management provides a basic level of security for any device that accesses corporate data. Collected device data can help administrators make more informed security and policy decisions about how to manage devices in their organization. More specifically, this feature will help administrators:
- Get a clearer picture of all the devices accessing corporate data.
- Use more comprehensive data to analyze device access in your organization through reports and security centers. For example, you can use it to identify devices that require operating system updates.
- Use more comprehensive data to analyze device access in your organization through reports and security centers. For example, you can use it to identify devices that require operating system updates.
- Take remedial action to remotely log out users when devices are lost, stolen, or compromised.
In addition, the Exclude Endpoint Verification filter that excludes in the device list can help increase endpoint verification implementation and ease with Context-Aware Access implementation
How to get started
- Admin: Refer Basic device management.
- End users: Nothing to do
Additional details
Basic desktop management that provides device information without apps or installers
When basic device management is enabled, administrators receive information about a limited set of device attributes: device type, device model, OS version, first sync, and last sync .
This will show up in two places in the Admin Console:
- List of devices found at Admin console > Device management > Devices > Endpoints.
- The test section is found at Admin console > Reporting > Audit > Devices.
Information about devices with basic device management will be listed along with devices that use other agents to provide administrators with detailed information about devices accessing corporate data . Administrators can filter the endpoint list by “Management Type” to see devices with a specific device management type, such as Basic, Endpoint Verification, or Drive File Stream.
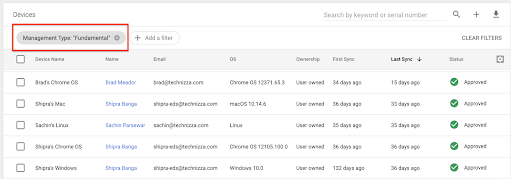
Limitations of basic device management and other endpoint verification options
Basic Device Manager is designed to be a lightweight, agentless crawler. Its goal is to provide a basic data set, which can help administrators make some decisions and add some control to the devices accessing their data.
Google provides other services, providing more granular data and allowing more comprehensive control for administrators, including Endpoint Authentication, Chrome Device management, Drive File Stream, and Mobile Management
New Endpoint Verification Filter helps implement Endpoint Verification and Context-Aware Access
We can also add filtering for devices without Endpoint Verification in the Admin console > Device management > Devices. This can help admins identify devices that are accessing corporate data without endpoint verification, and see if they want to install endpoint verification on any devices. This can also improve Context-Aware Access implementations. By viewing users and devices that do not have Endpoint Verification installed, administrators can identify and avoid potential user disruptions in advance. when Context-Aware Access is enabled.
Update: Gimasys